Module 1 part-2
Vulnerabilities ခွဲခြမ်းစိတ်ဖြာခြင်း
Multi-column
Vulnerability ဆိုတာဘာလဲ?
Refers to the existence of weakness in an asset that can be exploited by threat agents
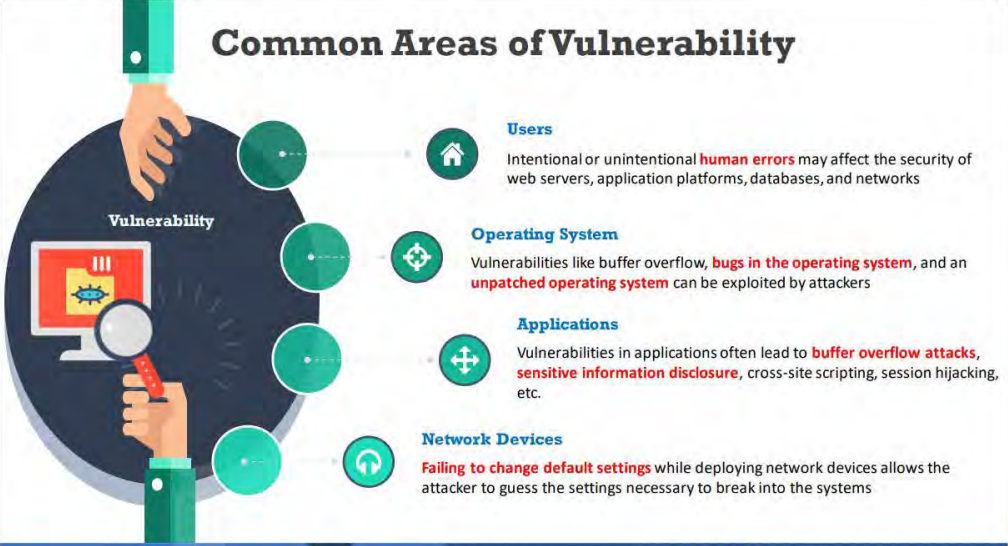
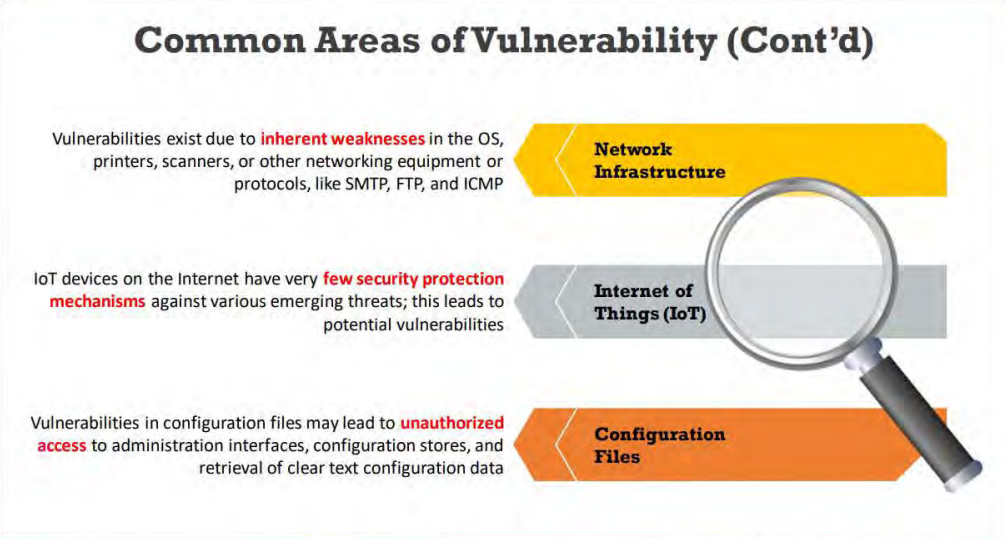
Common Reasons behind the Existence of Vulnerability
- 1- Hardware or software misconfiguration
- 2- Insecure or poor design of the network and application
- 3- lnherent technology weaknesses
- 4- Careless approach of end users
အားနည်းချက်ကြောင့်ဖြစ်လာနိုင်မည့်အကျိုးဆက်များ
- Hardware or software misconfiguration
- Insecure or poor design of network and application
- Inherent technology weaknesses(မွေးရာပါ)
- End-user carelessness(သုံးစွဲသူပေါ့ဆမှူ့)
- Intentional end-user acts(ဝန်ထမ်းဟောင်းမှ့အလွဲသုံးစားလုပ်နိုင်)
*စာမျက်နှာ 121 page 107 *
Multi-column
ဥပမာ-( ၁ ) Network လုံခြုံရေးအားနည်းတယ်ဆိုတာ
- Lack of password protection
- Lack of authentication
- Insecure routing protocols
- Firewall vulnerabilities
ဥပမာ-( ၂ )Network လုံခြုံရေးအားနည်းတယ်ဆိုတာ
- User account >> Originating from the insecure transmission of user account details such as usernames and passwords, over the network
- System account >>Originating from setting of weak passwords for system accounts
- Internet service misconfiguration >> Misconfiguring internet services can pose serious security risks. For example, enabling JavaScript and misconfiguring 11S, Apache, FTP, and Terminal services, can create security vulnerabilities in the network
- Default password >>Leaving the network devices/products with their default passwords and settings
- Network device misconfiguration >>Misconfiguring the network device
Multi-column
*စာမျက်နှာ 126 page 122 *
Multi-column
အားနည်းချက်ကြောင့်အထိနာနိုင်
- Information disclosure
- Denial of service
- Privilege escalation
- Unauthorized access
- Identity theft
- Data exfiltration
- Reputational damage
- Financial loss
- Legal consequences
- Hold footprints
- Remote code execution
- Malware installation
- Data modification
- Data loss
ဆိုးကျိုး
Risk = Asset + Threat + Vulnerability
ဥပမာ Example Of Risks
- Disruption or complete shutting down of the business
- Loss of productivity
- Loss of privacy
- Theft of information
- Legal liability (ဥပဒေအရ-တာဝန်ယူတာဝန်ခံမှူ့)
- Damage to reputation and consumer confidence(ဂုဏ်သိက္ခာနှင့် သုံးစွဲသူများ၏ ယုံကြည်မှုကို ထိခိုက်စေခြင်း)
*စာမျက်နှာ 131 page 116 *
အနောက်စာမျက်နှာသို့